Best Endpoint Security Software
-
PRODUCTS
-
BUYER'S GUIDE
Buyer's Guide
By Tamoghna Das, Market Analyst at SelectHub

Technology provides businesses with nearly endless opportunities for improvement and increased profitability. But those benefits can come at a steep cost. Every endpoint in your company is a chance to lose essential data. Luckily, endpoint security software mitigates that risk, putting control of your servers, laptops and other devices back in your hands.
In this buyer’s guide, we’ll discuss what endpoint security software is, its features and benefits, and how you can pick the best solution.
Executive Summary
- Enterprise endpoint security software helps businesses protect end-user devices against cyber threats and offers robust security measures necessary for running your operations.
- Top features include policy management, patch management, threat detection, offline data protection, data and media encryption, mobile security, and threat intelligence.
- Modern endpoint protection platforms are seeing a rise in AI, ML, behavioral analytics and UEM integration and will continue implementing zero-trust security frameworks.
- Make sure you list the required features and all questions about the software to ask the vendor before committing to a purchase.
- What Is Endpoint Security Software?
- Deployment Methods
- Primary Benefits
- Implementation Goals
- Basic Features & Functionality
- Advanced Features & Functionality
- Current & Upcoming Trends
- Software Comparison Strategy
- Cost & Pricing Considerations
- Best Endpoint Security Software
- Questions To Ask Yourself
- Questions To Ask Vendors
- Next Steps
- Additional Resources
What Is Endpoint Security Software?
Endpoint security software is a comprehensive suite of solutions that protects endpoint devices and networks against malware and cyberattacks. Generally, these systems deliver a multifaceted approach integrating scanning, detection and infiltration prevention.
Depending on the endpoint security vendor you select to fit your unique demands, you can expect numerous modules like advanced protection, mobile and server security, device control and policy, and patch and configuration management.
Here is a list of what enterprise endpoint protection software can do for your business:
- Detect, deter and neutralize malware, zero-day exploits and other infections.
- Diagnose and treat security issues.
- Manage IT infrastructure and user hierarchies.
- Handle devices and equipment to prevent device theft.
- Prevent data loss through effective encryption.
Software Types
1. Internet of Things (IoT) Security
The post-pandemic period has seen an increase in demand for IoT devices. With these devices playing an essential role in the day-to-day functioning of businesses, risk exposure can result in catastrophic consequences.
IoT security prioritizes the protection of these devices with secure SSL connections, policies, commands and rules.
2. Endpoint Detection and Response (EDR)
EDR software continuously monitors your endpoints for anomalies, threats and suspicious activities. With automated alerts and remediation controls in place, EDR is one of the most popular types of enterprise endpoint security.
It provides granular visibility into endpoint behavior and is your best bet to stop cyberattacks preemptively.
3. Network Access Control
This software acts as a powerful deterrent against insider threats. Classifying which users and devices have access to what part of your network is important.
While no endpoint security software can control the behavior of malicious users, you can use firewalls and access codes to limit access based on user roles.
4. Web Browser Security
According to a report by Verizon, web application attacks make up 26% of all cybersecurity breaches.
It may not be feasible to restrict access to the internet, so web browser security allows connected endpoints to safely browse the internet using URL filtering and browser isolation.
5. Sandboxing
This is a rather unique solution in which your endpoint security software replicates a typical end-user UI to test specific endpoints before allowing them access to the network.
6. Email Security
These days, you can access your email from almost any endpoint – your smartphone, smartwatch, home assistant and even your refrigerator. While it’s all very convenient, it exposes you and your endpoints to potential threats.
A secure email gateway helps you monitor all incoming and outgoing emails for malware and exploits.
7. Data Loss Prevention (DLP)
Data loss prevention is all about blocking restricted content from going out of the organization and enforcing data-sharing policies. It helps prevent instances like employees downloading client records, hackers trying to upload bank details on the cloud and other unauthorized attempts to access and share data. DLP software allows you to comply with security and privacy regulations.
8. Endpoint Antivirus Software
And last but not least, endpoint antivirus software. It checks file signatures in real time to prevent malware and other malicious threats from entering your system.
However, tracing threat signatures against a risk intelligence database can be somewhat traditional and expose you to more advanced cyberattacks.
Importance
Today, data is one of the most critical business assets that can add tremendous value to every facet of your organization. However, the increasing number and variety of endpoints pose a massive risk to corporate data security. Data loss and theft bring financial, reputational and regulatory damages to individuals and enterprises.
Additionally, a paradigm shift towards online infrastructure, remote working environments and increasing volume and complexity of cyberattacks have exponentially increased cybercrimes. Deploying appropriate endpoint security software can help you overcome these challenges and protect your entire security framework.
Endpoint security products provide round-the-clock protection to your endpoints, even when the devices are offline.
It’s not a matter of simply protecting you from malicious elements – endpoint security software leverages machine learning and AI to not only detect and deter new attacks but also predict future threats.
Cyber security threats are continually evolving, and enterprise endpoint security ensures you have access to the latest intelligence without compromising on scalability.
Challenges
Like any other software category, endpoint security software comes with its own challenges.
Resources
These solutions often intrude into your existing systems and create noise. This can impact your device’s performance and hinder other activities. While selecting endpoint security software, consider how much memory is available and what amount of storage the platform requires. However, we suggest investing in a solution that can run at its top performance without using too much space.
Administration
For enterprise-grade solutions, deployment, administration, updates and maintenance can be prominent factors. Some solutions offer a remotely accessible console to provide regular updates and monitor endpoints. All these tasks require an administrator to perform or oversee these operations. While large companies with ample resources can appoint an administrator, smaller companies bear the brunt. Nevertheless, they can use a basic system that doesn’t require frequent changes.
Scalability
Which solution is appropriate for you depends on how many and what kind of endpoints you need to protect. For enterprise-grade solutions, protecting thousands of endpoints from servers to manual devices is not a difficult task. However, they are expensive, and you must consider the scalability of these devices while investing.
Detection Efficiency
Endpoint protection platforms are responsible for defending your digital assets against cybersecurity threats, and threat detection plays a significant role in this process. Several solutions report a low detection rate, which is counterproductive. Some can be unnecessarily aggressive, providing false positives and causing alert fatigue. Find a solution that strikes a good balance between these two factors.
Expert recommendations and analysis of the best Endpoint Protection Software
Deployment Methods
While integrating security software, you can choose between cloud-based or on-premise deployment strategies, depending on your business priorities. Each method has its pros and cons, but today companies are widely opting for cloud-based models due to the broad spectrum of opportunities they offer:
Cloud-Based
The cloud comes with numerous advantages that make it a great alternative to traditional systems:
Pros
- Fewer in-house resources are required.
- Device monitoring from any location.
- Easy installation and less downtime.
- Automatic backups for increased security.
- Effective patch management.
- Shared risk intelligence on the latest trends and threat behavior.
Cons
- Relies heavily on internet connectivity, restricting the company’s access to network monitoring and data files in case of a connection failure.
- Lack of user control over networks and data.
- The chances of data breaches are higher in cloud networks.
On-Premise
On-premise systems may be falling in popularity due to the increased value of a remote workforce, but they offer certain advantages that businesses may find particularly useful:
Pros
- In-house deployment provides complete control over security.
- Reliable and independent of internet connection.
- Highly customizable due to on-site housing.
- Cost-effective over an extended period of time.
Cons
- Complicated administrative processes to maintain all devices.
- Requires constant security patch upgradation and monitoring.
- Limited scalability and customization.
Hybrid
A hybrid solution of both cloud-based and on-premise integrations is also available. You can utilize it to fulfill specific use cases and get the best outcome from both models.
With different deployment methods available in the market, your unique business needs and requirements should guide your final choice of endpoint software.
Expert recommendations and analysis of the best Endpoint Protection Software
Primary Benefits
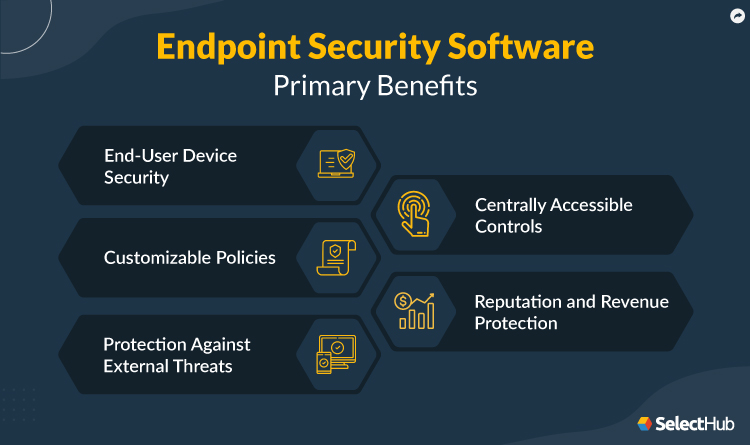
End-User Device Security
Enterprise endpoint security suites protect end-user devices within your company, including desktops, laptops, workstations, servers, mobile devices and any other device with an internet connection. This type of software protects devices from external threats — however, many companies primarily focus on protecting against internal risks.
Customizable Policies
Endpoint software provides a set of customizable policies for your employees regarding data access. For instance, your system administrator can use endpoint software to set up protocols to access certain information or download specific file types. These protocols prevent employees who don’t need vital data to do their job from obtaining access.
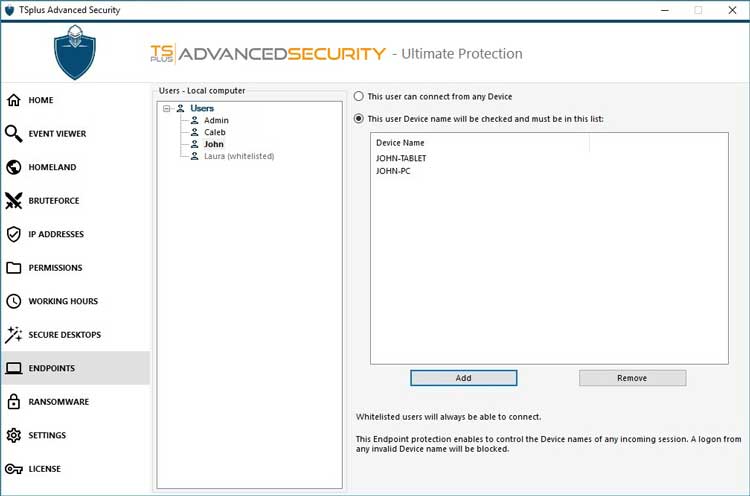
Customize policies for specific endpoints. Source
Protection Against External Threats
Endpoint protection software also works to ward off external threats such as malware. These systems perform this task through various detection technologies and web filtering capabilities. These features prevent your employees from stumbling upon websites that trick users into downloading harmful threats. However, even if a threat makes its way onto your device, endpoint protection suites can detect and remove it.
Centrally Accessible Controls
Administrators can get complete visibility into security controls and risk definitions with enterprise endpoint protection. Just like any other catastrophe, security breaches and exploits are unlikely to consider your convenience. In order to address this problem, endpoint software comes equipped with a centrally accessible control console. Imagine how restful your sleep can be, knowing your risk owners can resolve any issue immediately from anywhere in the world.
Reputation and Revenue Protection
Did you know the global average data breach cost is $4.35 million? This cost, however, is just the tip of the iceberg compared to the cost you might have to bear due to reputation loss. With the comprehensive protection that endpoint security provides, you can improve your company’s reputational value and bottom line.
Expert recommendations and analysis on the top Endpoint Security Suites
Implementation Goals
While security and control are the main objectives of endpoint software, you likely have more specific to achieve with implementation. Some tasks security software can help your organization achieve are:
|
Goal 1 Create access hierarchies |
You might require device-based policies to create access hierarchies sufficient for your business. These hierarchies restrict access based on which device an employee is using. However, for increased security, other companies might require user-based policies. This would ensure only employees with proper credentials can access data, regardless of device. You can learn more about policy management later in the guide to help you devise your necessities. |
|---|---|
|
Goal 2 Prevent internal data leaks |
Policy management can also help accomplish goal number two, but there are specific features to help with data loss prevention (DLP). Between device monitoring and remote access to endpoint devices, there are different ways you could create your requirements to meet expected goals. |
|
Goal 3 Prevent and address external threats |
Additionally, the level of protection against external threats can vary from system to system. For some companies, external threats are a major priority. However, many companies are also content with the level of protection provided outside of their solution. It’s important to include what features you need on your list to get the perfect endpoint software for your company. |
These goals are common among all endpoint security software buyers, but how your business achieves them will be unique. The only way you can ensure your business reaches its implementation goals is if you take the time to craft a detailed requirements list of the must-have features and other considerations for your security needs.
Expert recommendations and analysis on the best Endpoint Protection software
Basic Features & Functionality
Although every solution is different, there are a few common features most, if not all, endpoint software systems include:
| System Administrator Portal |
Portals are an important piece of security on an enterprise level. Enterprise endpoint protection software provides your system administrator with a portal from which they can manage all devices. This is especially useful for companies with small IT departments and large or multiple offices. It allows administrators to configure security settings for large groups of devices, eliminating the time it would take to do this individually for each device. |
|---|---|
| Policy Management |
Administrators can create policies, set access hierarchies and ensure employees don’t have access to data that extends beyond their needs. They can also set policies based on the device or user and create override policies. This feature is useful when a C-level executive needs access to data not already available on the device they are using. Many solutions provide audit trails and alerts when they override a policy to prevent override abuse. |
| Patch Management |
Patch management ensures your operating systems and applications are regularly updated. Providers release patches to fix weaknesses in the system as soon as they discover them. However, not everyone is as mindful of patches and will often continue using older software versions. Unpatched applications provide attackers with the perfect opportunity to strike. If you’re not routinely updating your software, your data is easier to compromise. Patch management allows your system administrator to schedule updates remotely outside of working hours. This ensures you always keep your software updated without any extra effort from your employees. |
| Threat Detection |
Even with strong preventative measures in place, it’s not impossible for malware or other malicious traffic to make their way onto your devices. When this occurs, it’s extremely valuable to have a system in place that can detect threats and alert the system administrator. Further, many endpoint software will detect threats and remove them automatically. |
| Device Monitoring |
Similar to how your system administrator can mass update your devices, they can also remotely monitor and control other aspects of your endpoints. This feature lets administrators monitor all devices connected to your company’s endpoint. Some of these include local disks, USB and Bluetooth-connected devices and even cloud servers. In addition to monitoring the devices above, administrators can set permissions for which ones the end-user can implement. For example, your system administrator might allow a USB keyboard but not a USB flash drive. |
| Virtual Environments |
A virtualized environment lets businesses use one piece of hardware for multiple functional purposes. Think of it as a guest user on your personal computer. In reality, there’s only one computer, but effectively there are two systems. Security solutions protect these virtual environments, even if they exist on the same hardware. With an endpoint solution, a compromised virtual environment won’t affect other environments. |
| Mobile Security |
Mobile devices have become prevalent in businesses worldwide, and as such, your business needs to take measures to protect them. However, mobile devices are utilized in different ways than a PC might be. This calls for security measures specific to mobile interfaces. These solutions allow administrators to restrict individual applications and monitor user activity. Additionally, administrators can set the amount of time a mobile device remains unlocked while unattended. Lastly, they can set passwords, disable camera use and remotely wipe data. |
Expert recommendations and analysis on the top Endpoint Security Software
Advanced Features & Functionality
In addition to the basic features endpoint security software provides, these extra features can help your business customize the desired level of security.
| Data and Media Encryption |
This feature encrypts any data downloaded or sent without authorization. This is helpful, as seen above, when an unapproved party attempts to steal information offline. Information downloaded onto a physical device while offline can be encrypted. It locks files that are technically stored on the device for everyone without the encryption key. You can execute encryption when a device is online as well. When protected files are sent through email or peer-to-peer platforms, the files will be inaccessible without a key. |
|---|---|
| Advanced Security |
Even though device monitoring and encryption are great ways to prevent data leaks, they don’t protect against more complex threats from outsiders. These threats include many types of malware like viruses, worms, spyware, trojans and rootkits. Malware either attacks your endpoint directly or works to steal passwords and sensitive information. To prevent this, you'll need enterprise antivirus software. Advanced systems use specialized technology to detect these threats, and in many instances, remove them. Additionally, endpoint software prevents users from accidentally inviting malware into the system in the first place. Web filtering and application blocking can provide more malware protection than you think. |
| Server Security | When people think of endpoint devices, servers aren’t always the first piece of equipment that comes to mind. However, servers are incredibly important, and you must consider them when shopping for a new system. This feature prevents threats to your email, gateways, files and collaboration servers. |
| Endpoint Detection and Response |
Modern and sophisticated threats like phishing, fileless malware, polymorphic malware, ransomware and more can easily bypass the security perimeter, demanding granular visibility and control to safeguard your security infrastructure before and after infection. EDR is a layered security strategy that integrates continuous monitoring and endpoint data with rule-based automated response and analysis capabilities. Organizations can determine potential cyber threats, remove or contain incidents, further investigate and provide essential remediation recommendations to restore infected systems. A proactive EDR security approach, alongside your endpoint software, can help you maintain a proper security posture. It offers fundamental capabilities that include complete visibility throughout the IT environment, data collection to create a threat repository, behavioral protection and real-time responses. |
| Threat Intelligence |
Threat intelligence is a key aspect of cybersecurity utilized by IT specialists to examine and analyze emerging or existing threat actors. You can use gathered raw data to identify emerging threats and known indicators of compromise (IOCs), create effective defense mechanisms and mitigate security risks. You can protect your organizations against advanced persistent threats, zero-day attacks and exploits. Organizations can stay updated about threat methods, vulnerabilities and targets and become more proactive against future security threats to prevent any financial and reputational damage. |
Expert recommendations and analysis on the top Endpoint Security products
Current & Upcoming Trends
Endpoint security has evolved over the years with the regularly changing volume and sophistication of cyber threats. New security solutions continue to advance with changing business needs to combat the latest changes and trends.
For an in-depth look at where the industry is heading, check out our article on the top trends in cyber security.
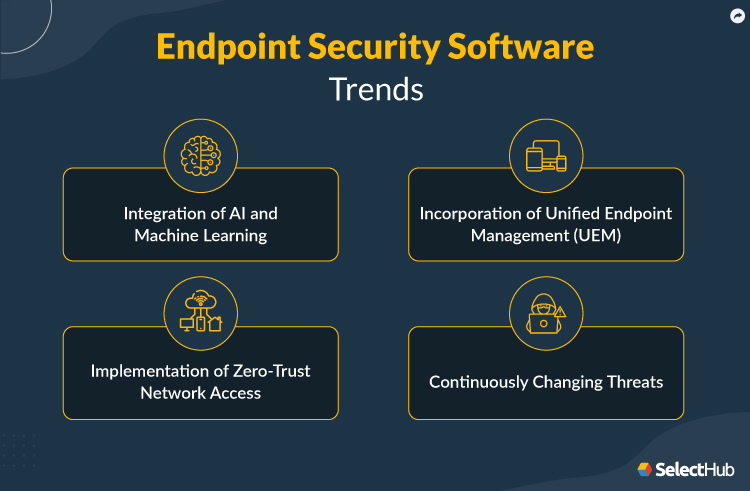
Integration of Artificial Intelligence and Machine Learning
The demand for complex security automation has increased with evolving threats for examining traffic and predicting and blocking attacks. Solutions using artificial intelligence and machine learning can detect false positives and negatives produced by robotics analysis.
These advanced technologies can strengthen early detection capabilities using threat intelligence and behavioral analysis. Artificial intelligence can detect potential attack variants, and machine learning aids in identifying attack classes and detecting threats.
Implementation of Zero-Trust Network Access
The shifting focus on operational systems is forcing organizations to implement zero trust security frameworks (ZTNA) with web security, network security and identity access management (IAM). We expect to see this ongoing trend grow in the foreseeable future.
The global zero trust security market is projected to reach $60.7 billion by 2027, registering a CAGR of 17.3%. Vendors are equipping their ZTNA applications with greater flexibility, role-based adaptability and improved persona.

Incorporation of Unified Endpoint Management (UEM)
Unified endpoint management (UEM) solutions combine identity management, endpoint security and remote management, saving resources for you to invest in different systems. Nowadays, CISOs increasingly implement endpoint security with integrated UEM modules. Like ZTNA frameworks, UEM solutions have also evolved in the past few years.
Modern solutions have customizable features that enable device management, supporting a wide range of operating systems and devices. They also offer frequent and multiple patch and software updates.
Continuously Changing Threats
A rapid increase in relentless attack vectors like fileless malware, zero-day attacks, cryptocurrency mining and other threats that pose unfamiliar risks and damage valuable resources worldwide. Safeguarding your devices from such vectors requires a regularly updated security environment and a layered defense approach to security.
Expert recommendations and analysis on the top Endpoint Software
Software Comparison Strategy
Implementing robust endpoint security software is crucial to strengthen your system controls, existing policies and risk management functions. However, the endpoint software market has a wide range of vendors offering various tools and technologies to block threats from attacking your corporate devices. Some systems specifically support large enterprises, whereas others are better fits for small and medium-sized organizations.
In order to find the right solution for your company, it’s important to perform a full comparison of the best endpoint protection software you’re considering.
Integrated Modules
The seamless collaboration of data and information across various modules is critical for quickly identifying, preventing and remediating advanced threats. Several providers now offer common data exchange architecture, UEM and zero-trust framework to strengthen your endpoint protection platform’s capabilities. However, if your endpoint security requirements are limited, you can deploy software without all these integrations.
Deployment Model
Based on your company’s structure, you must find an appropriate deployment model. As discussed previously, every deployment model has its own unique pros and cons. We suggest considering the costs, maintenance and capabilities of cloud and on-premise modes and making an informed decision to get the best out of your software.
Advanced Features
Modern capabilities like AI, machine learning and advanced security help endpoint solutions boost their efficiency. They also let you quickly detect zero-day attacks and advanced persistent threats. Along with a real-time threat intelligence feed, they offer all-around protection. This is why you should look for advanced features in your shortlisted solutions.
Luckily, SelectHub’s analyst team has already evaluated and ranked some of the top endpoint security providers by how well they fulfill the features listed above. See our in-depth endpoint security software comparison report for a summary of each provider’s capabilities to find the best endpoint software for your business.
Cost & Pricing Considerations
Endpoint security software vendors charge on a per endpoint basis rather than the user. Enterprise or premium solutions that include advanced security technologies and premium customer support options are priced higher than basic products.
The costs of endpoint security suites vary primarily according to your deployment strategy. On-premise solutions come with the cost of hosting and maintaining the system. You require a dedicated server to host the software and monitor endpoints, along with a team of IT security experts. However, additional infrastructure or staff isn’t necessary for cloud-based endpoint security products as they are hosted directly on the vendor’s servers.
Mostly, cloud-based systems charge on a per-month basis. On the other hand, on-premise solutions require buyers to pay the entire cost upfront, but as we mentioned earlier, these systems could save you more if you plan to use them for a longer duration.
You can segregate the pricing of most endpoint security software into three pricing ranges:
- $0.90 to $4
- $5 to $8
- $8 and more
While narrowing down your software choices, your cybersecurity budget plays a critical role. Depending on the size of your business and what requirements you want to fulfill, take time and choose wisely before investing in an endpoint software solution.
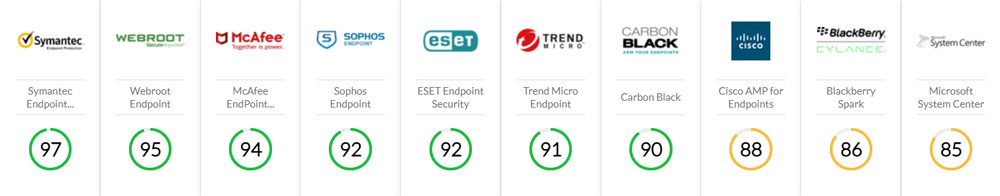
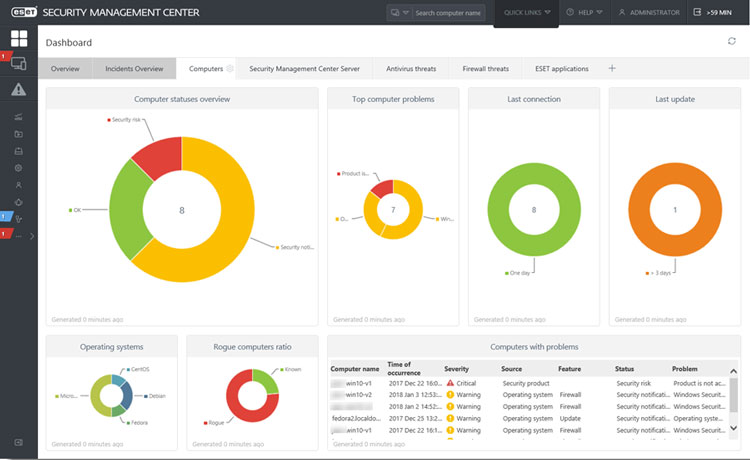
Best Endpoint Security Software
Now that you know what endpoint security software can do, how do you decide which product is the best choice for your needs? Jumpstart your software search with our research team’s list of the top five endpoint security software products.
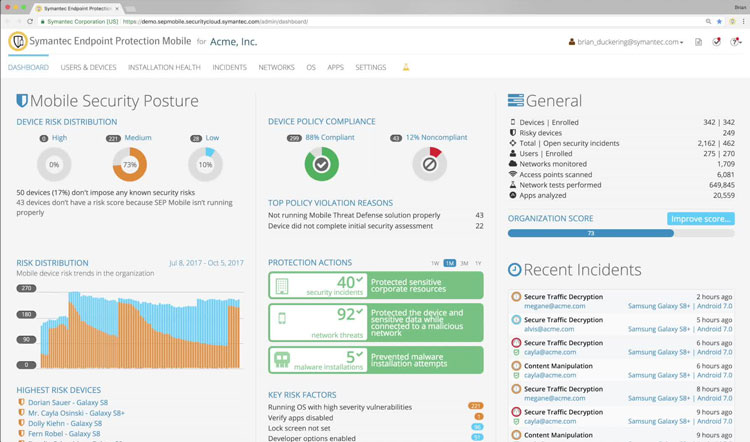
Symantec Endpoint Protection
Symantec is a leading endpoint protection platform that protects your complete security infrastructure, including endpoints, networks, email and the cloud. It offers on-premise or cloud-based solutions for comprehensive security through endpoint, information and web security services.
Top features include anti-malware, anti-ransomware, compliance, data protection and storage protection. Its multi-layered defense system can reduce the attack surface and prevent lateral movement and botnet connections.
Safeguard mobile devices.
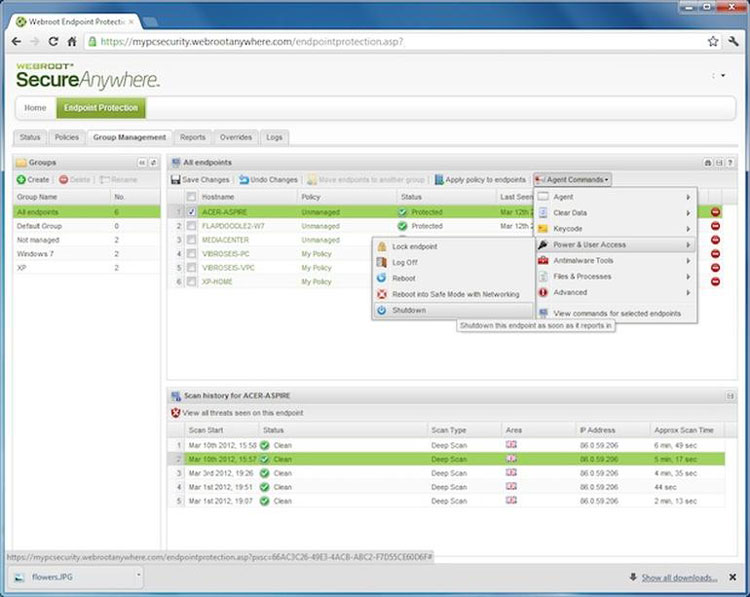
Webroot Endpoint
Webroot’s endpoint protection software stops sophisticated cyberattacks, streamlines management and maximizes profitability. Its integrations with PSA, RMM and BI platforms make it suitable for MSPs and businesses of all sizes.
It can prevent known threats and unknown zero-day attacks through a combination of innovative file patterns, predictive behavior recognition capabilities and cloud computing. Its evasion shield can also protect against file-based and fileless script attacks. Other capabilities include threat detection and remediation, simple setup interface, data reporting, evasion shield, and DNS protection.
Create groups to manage endpoint devices.
McAfee Endpoint Security
McAfee delivers a wide range of solutions for enterprises and home users. It combines digital security with advanced identity and privacy protection. Its cloud-based endpoint protection software secures data and blocks threats across the network, cloud, devices and on-premise environment.
Its widespread global threat intelligence network can analyze and collect data from more than 500 million endpoints. It synchronizes protection, detection and correction through cloud security, security analytics, machine learning and SIEM capabilities. McAfee’s key capabilities include search engine and content file scanning, security agent module, ePO, threat prevention, and adaptive threat protection (ATP).
Gain visibility into overall security metrics.
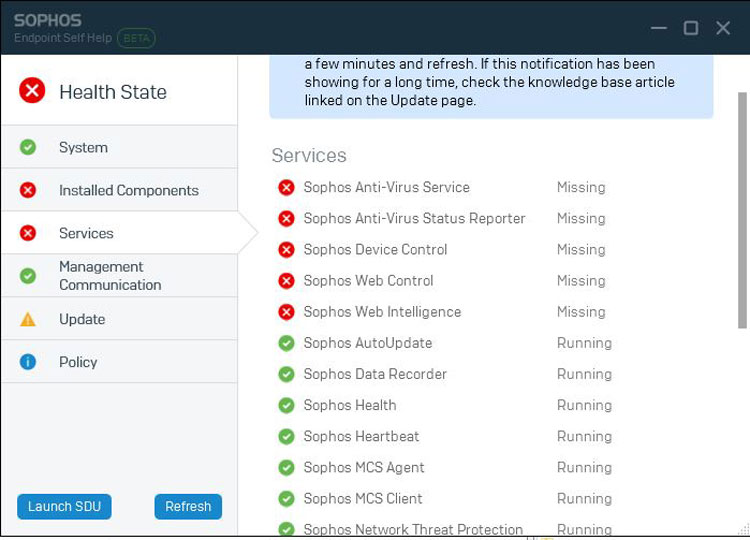
Sophos Endpoint
Sophos endpoint leverages deep learning to detect known and unknown malware. Its anti-ransomware technology can identify and stop malicious encryption processes. It can also safeguard devices from file-based and master boot record ransomware. Sophos offers both on-premise and cloud-based deployment.
It offers an extensive set of features that include endpoint detection and response, exploits prevention, managed threat response and active adversary mitigations in a single solution. The platform also provides next-generation capabilities such as adaptive active adversary protection, built-in ZTNA agent, Linux malware protection enhancement and frequent account health checks.
See which security options are disabled or unavailable.
ESET Endpoint Security
ESET delivers a multi-layered security solution that can combine machine learning with human expertise to guard your devices against ransomware. It offers home as well as enterprise-grade solutions that help find advanced persistent threats, block targeted and fileless attacks, and prevent data breaches. You can deploy the platform on-premise or in the cloud, and it supports Windows, iOS and Linux.
It provides users with a variety of capabilities, including behavioral detection, network attack protection, ransomware shield, advanced memory scanner, in-product sandbox, exploit blocker, two-way firewall and botnet protection.
Dashboards display security information.
Expert recommendations and analysis on the top Endpoint Security Software
Questions To Ask Yourself
Use these questions as a starting point for internal conversations:
- Where do you want to deploy the software?
- What are your objectives and requirements?
- Who will use these endpoint security services, and what are their desired features?
- How much technical assistance do you require for implementation?
- What’s your cybersecurity budget?

Questions To Ask Vendors
Use these questions as a starting point for conversations with vendors:
About the Software
- How much visibility does your product provide?
- What devices does your system protect?
- How often are updates released, and how do they roll out?
- What’s the learning curve to understand and run your endpoint software?
- What kind of integrations does your solution support?
About the Vendor
- What’s your success rate with your everyday users?
- What exactly does your solution protect against?
- How scalable is your solution?
- What support or training do you provide?
- Do you offer industry-specific solutions?
Expert recommendations and analysis on the top Endpoint Protection software
Next Steps
Selecting the right endpoint security software is critical to the safety of your data and business assets. Formulating a list of requirements with valuable input from key stakeholders and comprehensive provider analysis is required to create a safe digital environment. This guide can be used as a starting point to help professionals make the right decision.
If you need further help, check out our comparison report for more information on the top endpoint security software leaders in the industry. Good luck!
Additional Resources
- What Is Endpoint Protection?
- Top Endpoint Security Requirements and Features
- What Is an Endpoint Protection Platform (EPP)?
- What Is Next-Generation Endpoint Security?
- Benefits of Cloud Endpoint Security Solutions
- Best Endpoint Security Vendors
- What Is an Endpoint?
- What Is Unified Endpoint Management (UEM)?
- What Is Endpoint Monitoring?
- Endpoint Antivirus vs Endpoint Security
Top 10 Endpoint Security Software Leaders by Analyst Rating (of 142 products)
(of 142 products) GET THE IN-DEPTH REPORTProducts found for Endpoint Security Software
Malwarebytes EDR

Malwarebytes EDR is a cybersecurity platform that provides users with a comprehensive suite of solutions to keep devices safe. It crushes the latest threats and malware using multiple layers of technology like anomaly detection, behavior matching and application hardening. It is the first layer of defense against viruses and hackers which shields devices, data and privacy. Its default server policies with predefined configurations simplify and improve platform security posture. It delivers various detection and remediation capabilities to home users and businesses of all sizes.
Symantec Endpoint Protection

Symantec Endpoint Protection was built to protect users and enterprises from malicious actors and harmful software. It’s ideal for small or medium-sized businesses. This system comes with a standard set of protection features, as well as several non-standard, unique capabilities that help this product to stand out from its competitors. Features include intrusion prevention, firewall and anti-malware features.
ESET Endpoint Security

ESET Endpoint Security is a data protection product based out of Slovakia that is ideal for businesses of all sizes. The product provides a full range of endpoint protection features to help it stay on top of known and unknown threats. Encryption, server security, two-factor authentication, leak protection, threat protection and more are all included in the software package.
Webroot Endpoint

Webroot Endpoint Protection is business-grade cybersecurity solution made for small businesses, as well as any managed services provider that manages SMBs. In addition to a suite of highly effective features to protect against threats, Webroot also provides centralized cybersecurity management, flexible billing and smooth integrations with other systems.
McAfee EndPoint Security

McAfee Endpoint Protection is a digital security and malware defense software that covers most users’ security needs in a single package, from web threats to applications. It offers a number of standard features to equip enterprises with the tools they need to manage their business. Features like integration, machine learning, automation and more help businesses stay on top of their enterprise. It is affordable and scalable to companies of any size.
Kaspersky Security Center

Kaspersky Security Center provides business-grade digital security and malware protection for businesses of any size. With a suite of highly-effective features like automated hardening, easy separation of admin and user roles, and single-console, it can aptly serve SMBs as well as large enterprises, or any managed service provider.
Sophos Endpoint

Sophos Endpoint Protection is a signature-free malware and defense software, ideal for businesses of any size and software platform.The software contains a fully-featured antivirus suite, along with a series of capabilities to protect user devices from offline threats.
Panda Endpoint Protection

Panda Endpoint Protection provides its users with advanced, ever-evolving and dynamic cyber-security models with big data and artificial intelligence capabilities. It can detect, analyze, classify and block malware through its adaptive defense security model. Its next-gen anti-malware technologies based on behavior intelligence can replace traditional antivirus. It can safeguard the entire environment against non-malicious tools and other techniques like zero-day threats, APTs, targeted attacks and ransomware.
FortiClient

FortiClient is an integrated platform that provides users with multi-layered malware protection. It allows organizations to have complete visibility and control over hardware inventory throughout the security fabric. Its automated next-generation protection can identify and contain known and unknown threats. It is available with on-premise and web-based deployments and is designed for small and medium-sized businesses. Its behavior-based protection guards against known and unknown threats and prevents the exploitation of known vulnerabilities.
Trend Micro Vision One

Trend Micro Endpoint Security is a solution designed to help businesses protect their user devices. Trend’s offering provides a bevy of software features that result in a complete, multi-layered approach to endpoint protection. The app delivers standard endpoint protection features like advanced threat protection, anti-malware, encryption, device control, application whitelisting and more, on top of its unique features, like data-loss protection and instant messaging protection.
VIPRE Endpoint Security

VIPRE Endpoint Security delivers data and privacy protection to its customers against advanced and sophisticated cyber threats. Organizations can manage and safeguard the threat landscape via a cloud, server and site manager with a centralized management console. It helps MSPs and businesses of all sizes simplify operations, boost productivity and maximize efficiency.
Bitdefender GravityZone

Bitdefender GravityZone is a dedicated network and device security product that is tailor-made to defend against malware, viruses, zero-day attacks and more. It touts itself as being a “multi-layered” approach to device and network security, able to secure devices of any kind. It’s a singular approach that is ideal for businesses of any size, or any managed service provider that is serving a company.
Blackberry Spark

Blackberry Spark is a security software application that helps companies keep their entire threat landscape safe and protect against threats and malware. It uses artificial intelligence capabilities for threat detection. It offers a light footprint, robust device control and simple deployment. It is ideal for businesses of any size or scope, especially those deploying fleets of devices to its employees.
Palo Alto Traps

Palo Alto Networks Traps provides comprehensive protection to its users against unknown malware-driven attacks and sophisticated vulnerability exploits. It blocks threats and coordinates enforcement with cloud security and networks to safeguard against cyberattacks. Organizations can detect and respond to attacks using artificial intelligence and machine learning techniques. A multi-layered approach prevents malicious executables through a combination of policy-based restrictions, WildFire inspection and analysis and malware techniques mitigation.
Carbon Black

Formerly known as Bit9 + Carbon Black, Carbon Black Enterprise Protection is an endpoint protection software developed specifically to protect enterprises from advanced security threats. CBEP is comprised of three components, delivering comprehensive protection for businesses. CB Protection stops malware, ransomware and non-zero day attacks. CB Response is an advanced endpoint detection and response (EDR) tool, built around scalability and attack review. CB Defense is an antivirus combined with an EDR solution, delivered via the cloud.
Herjavec Group

Herjavec Group is a global cybersecurity firm that offers comprehensive protection to minimize threats and cyber attacks. It delivers expertise in security services, which include professional, managed, and identity and access management. In 2022, it merged with Fishtech to create Cyderes (cyber-defense-and-response).It’s designed for complex and multi-technology environments to protect business assets, including information, data, IT infrastructure and employees. It delivers a suite of cybersecurity modules to enterprise organizations. Specialized services include advisory services, security workshops, SOC operations, MDR, digital forensics and vulnerability management.
Cisco Secure Endpoint

Cisco Secure Endpoint Premier is a comprehensive cybersecurity solution designed to protect organizations from advanced threats. It combines Endpoint Protection Platform (EPP) and Endpoint Detection and Response (EDR) capabilities to deliver robust security. Key features include advanced threat detection, behavioral analysis, and integration with threat intelligence feeds, ensuring real-time protection against known and unknown threats. Users benefit from a user-friendly interface, scalable deployment options, and incident response capabilities. With cloud-native security, it safeguards endpoints across diverse environments. Cisco Secure Endpoint Premier is favored for its effectiveness in threat mitigation and its ability to provide visibility, control, and compliance assurance, making it a valuable asset for organizations of varying sizes.
Comodo Endpoint Security

Comodo Endpoint Security provides its users with complete protection against internal and external threats by combining advanced security technologies in a single, unified platform. It safeguards businesses of all sizes against cyber threats and malware with a seven-layered defense approach that includes antivirus, firewall, host intrusion prevention, auto-sandbox, web URL filtering, file reputation and behavioral analysis.
Catapult Systems

Catapult Systems is a digital services firm that builds and sustains IT business solutions. It provides users with Microsoft-focused inclusions that specialize in digital transformation and cloud-based technologies. It is designed for mid and large-size organizations to solve complex business challenges.
CrowdStrike Falcon

CrowdStrike Falcon is a digital security and endpoint defense product. The company is well recognized in its industry, playing a key role in the cybersecurity space and investigating major breaches like the Sony Pictures hack and the 2016 Democratic National Convention hack. With an assortment of standard and unique features and flexible pricing, it is built for businesses of any size.
Avast Business Antivirus

Avast Business Antivirus is a cybersecurity platform that provides its users with proactive antivirus inclusions to protect their organizations from ransomware and advanced cyberattacks. It can secure, manage and monitor complex networks using a global threat detection network. It is designed for IT service providers and small to medium-sized businesses. It safeguards Windows, Windows Servers, Mac and Linux devices against sophisticated cyber threats using a next-generation security approach and cloud-based analytics.
Microsoft System Center

Microsoft System Center, originally Microsoft Forefront Endpoint Protection, is software that helps IT managers oversee their network and infrastructure, protect against threats, secure data and more.It brings a bevy of features that help it stand out from its competitors, such as hybrid deployment, hyper-converged infrastructure and HTML5 dashboards.
F-Secure Protection Service for Business

F-Secure Elements Endpoint Protection, formerly known as F-Secure Protection Service for Business, is a cloud-native platform that helps companies eliminate malware, reduce the attack surface, block targeted threats, prevent zero-day attacks and manage vulnerabilities. It leverages heuristic analysis technology to manage and detect breaches in mobile devices, computers and servers from a single location.
eSentire

eSentire provides organizations with dedicated threat detection and response, safeguarding businesses from known and hidden threats across their attack surface. It leverages a proprietary AI methodology for threat hunting and advanced automation, eSentire’s innovation in the MDR industry solves some of cybersecurity’s biggest challenges. Security is not only a data volume but also a technology problem that requires a modern approach to AI and expert analysts. eSentire helps process massive amounts of data, providing full threat visibility and response to protect the business’s assets.
Comodo cWatch

Comodo cWatch is a cybersecurity platform that delivers comprehensive protection for websites, web applications and web servers with its six-layer stacked security solution. It ensures complete website protection with early detection, instant malware removal and proactive preventive methods. It is a cloud-based, managed security service that leverages actionable intelligence to protect networks against malware, blacklisting, hacking and more. It can be used with any CMS, regardless of size or purpose.
Netsurion

Netsurion offers robust cybersecurity solutions, catering to businesses seeking comprehensive threat protection. Tailored for mid-sized enterprises, its key features include advanced threat detection, network security, and compliance management. Users praise its seamless integration and user-friendly interface. A satisfied user notes, "Netsurion's proactive threat detection is unparalleled." While pricing considerations may be on the higher side, the consensus is that the value aligns with the investment. Users appreciate its performance, with one stating, "Netsurion outshines competitors in detecting and mitigating cyber threats." Overall, Netsurion emerges as a top choice for businesses prioritizing proactive cybersecurity measures, proving its worth against industry counterparts. Pros Advanced threat detection Robust network security Efficient compliance management Seamless integration User-friendly interface Cons Higher pricing May not suit smaller businesses Learning curve for new users Occasional update delays Customization limitations
AVG Internet Security Business Edition

AVG Internet Security Business Edition offers advanced antivirus protection against ransomware, spam, phishing and more. Organizations can manage online security with instant email alerts about threats and remote admin modules. It provides automatic updates and ensures safe surfing, data security and privacy protection. It offers a cloud management console to enable businesses to deploy security to various devices, manage policies, schedule updates and monitor threats from a single location.
Desktop Central

Desktop Central is a web-based software application that lets administrators manage computers efficiently, from a central point. It provides unified management inclusions that help with managing tablets, smartphones, laptops, desktops and servers. It allows users to automate routines like deploying software, installing patches, imaging and deploying OS, monitoring software usage statistics, managing assets and USB device usage, software licensing and more. It’s ideal for small to large-sized enterprises.
Cloudflare

Cloudflare is a web infrastructure and website security platform that delivers a wide range of network services to businesses of all sizes to increase security and enhance performance. It safeguards and ensures the reliability of external-facing resources like applications, APIs and websites. It helps users develop globally-scalable inclusions and protect internal resources such as teams, devices and firewall-protected apps. It offers content delivery network services, comprehensive DDoS protection, distributed domain name server services and internet security.
Carbonite

Carbonite is a cloud-based backup and recovery software application that provides its users with multiple solutions for secure and reliable protection of any data type ranging from onsite, cloud and hybrid backup to high availability and document retention. It helps boost digital fitness with a customized cyber resilience strategy. It offers flexible deployment options and personalized protection covering a wide range of business requirements. It is designed for individuals and small to large-sized enterprises.
GoSecure
GoSecure is a managed detection and response service provider that helps enterprises protect their security environment against emerging, fileless and memory-based attacks. It delivers visibility across major threat vectors like email, endpoint, network, insider activity, web and combines it with threat intelligence and operational experience. It supports a cloud-based CounterTack module that lets organizations identify more threats, mitigate faster and reduce costs. Users can prioritize resources that deliver maximum value through managed security services. It also provides the security infrastructure needed to protect companies.
NowSecure

Nowsecure is a mobile app security software organization that provides users with on-premise or cloud-based automated solutions, managed services and expert penetration testing. It delivers comprehensive automation techniques that can manage mobile risk, reduce costs and boost growth. It can identify a wide range of compliance gaps, privacy issues and threats in commercial, business-critical and custom-developed mobile modules through advanced testing and analysis across various deployment models and devices. Its additional layer of products and services can serve customer groups, specific sectors and latest technology opportunities.
NCC Group

NCC Group is a global information assurance firm that offers expertise in cybersecurity and risk mitigation. It provides organizations with a suite of services to recognize, evaluate, mitigate and respond to the cyber attacks. It offers remotely-deployed services to address security challenges. Users can build a cyber-resilient organization and protect it against the ever-evolving threat landscape. It’s designed for both public and private sectors, including governments.
Avira Prime

Avira Prime is a security suite that helps users detect malware in real-time, enhance the speed of devices, encrypt web browsing and protect passwords. It supports PC, Mac, iOS, Android and web browsers. It offers multiple functionalities to prevent payment fraud, block phishing attacks, save cost on online purchases, boost device memory, stream content globally, safeguard private data and more-
SpyBot

Spybot is a computer program that helps users detect and eliminate spyware and malware to safeguard their privacy. It blocks online advertisements that display during installation. It’s compatible with Microsoft Windows. Customers can repair the registry, trojans, tracks, trackerware and other malware. It prevents spyware installation by modifying the host file.
GlassWire

GlassWire is a network monitoring and security tool that helps customers detect hidden threats with a built-in firewall. It safeguards data, devices and privacy by letting users view past and current network activities to detect and block threats or malware. It provides internet privacy protection, internet security, remote server monitoring, evil twin detection, extended graph histories and more. It includes pro, basic or elite upgrades, offering extra protection and safety.
Call SelectHub for a free 15-minute selection analysis: 1-855-850-3850
Best of Awards
COMPARE THESE LEADERSSelectHub analysts have spent over 2,000 hours evaluating over 300 endpoint security software solutions, ensuring we understand each software’s capabilities, strengths, and limitations. From this, we recognize which solutions really lead the pack, and deliver the features and capabilities companies actually need, based on crowdsourced requirements from the SelectHub platform.

Awarded to top products picked by Analysts as Overall Best Products in the Category.

Awarded to products receiving a User Sentiment Score of Excellent.

Awarded to the Top products scoring 80 or more in this feature.

Awarded to the Top products scoring 80 or more in this feature.

Awarded to the Top products scoring 80 or more in this feature.

Awarded to the Top products scoring 80 or more in this feature.
| Symantec Endpoint Security | Sophos Intercept X | Microsoft Defender for Endpoint | Kaspersky Endpoint Security for Business |
| Bitefender GravityZone | Trend Micro Vision One | Trellix XDR |

Awarded to the Top products scoring 80 or more in this feature.
| ESET PROTECT MDR | Sophos Intercept X | Trend Micro Vision One | Trellix XDR |
| Microsoft Defender for Endpoint | CrowdStrike Falcon | Cisco Secure Endpoint | Blackberry Cyber Suite |

Awarded to the Top products scoring 80 or more in this feature.

Awarded to the Top products scoring 80 or more in this feature.

Awarded to the Top products scoring 80 or more in this feature.

Awarded to the Top products scoring 80 or more in this feature.

Awarded to the Top products scoring 80 or more in this feature.
Real People... with Data
Narrow Down Your Solution Options Easily
closeApplying filters...
Search by what Product or Type or Software are you looking for